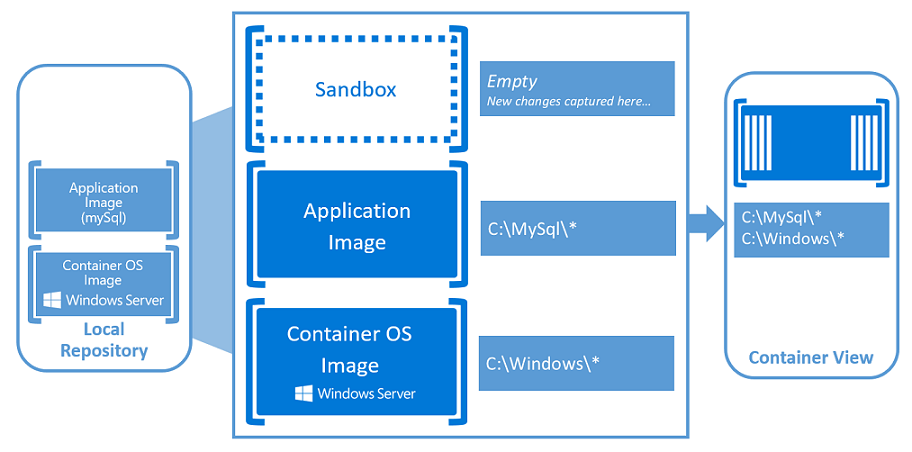
If you are experiencing problems with connecting to Office 365 or Exchange Online using Powershell after enabling Modern Authentication (Multi Factor Authentication) Check out this fantastic guide to solving the problem, and how you can add the information required to your Powershell Profile. All Credit to Cogmotive.com